what we do
We offer an end-to-end
cybersecurity that spots risks fast

Cybersecurity services
Security risk management. Accelerate direct-to-cloud user access and cloud services for your dispersed workload and workforce with a fast, reliable, and secure cloud-native Security Service.
SERVICES INCLUDE:
Provide and defend your network with the most reliable cyber-attack defence, protecting against sophisticated and damaging threat vectors.
Mitigate advanced email threats with actionable insights to help combat the rise in cyberattacks, detect email-based threat vectors and block attacks.
Provide comprehensive endpoint defence, protecting users from common threats, detecting advanced attacks, and empowering relevant responses.
Cloud services
Provide technical guidance and advice to enable our clients to understand, plan, and implement integrated Cloud solutions.
SERVICES INCLUDE:
Provide a full range of services and products in the cloud such as Microsoft 365, Microsoft Azure, Enterprise Mobility + Security (EMS) and much more.


Managed IT services
Provide and proactively manage a defined set of IT services for your infrastructure and line of business (LoB) applications, supporting strategies to help your organization to be highly resilient and cost effective.
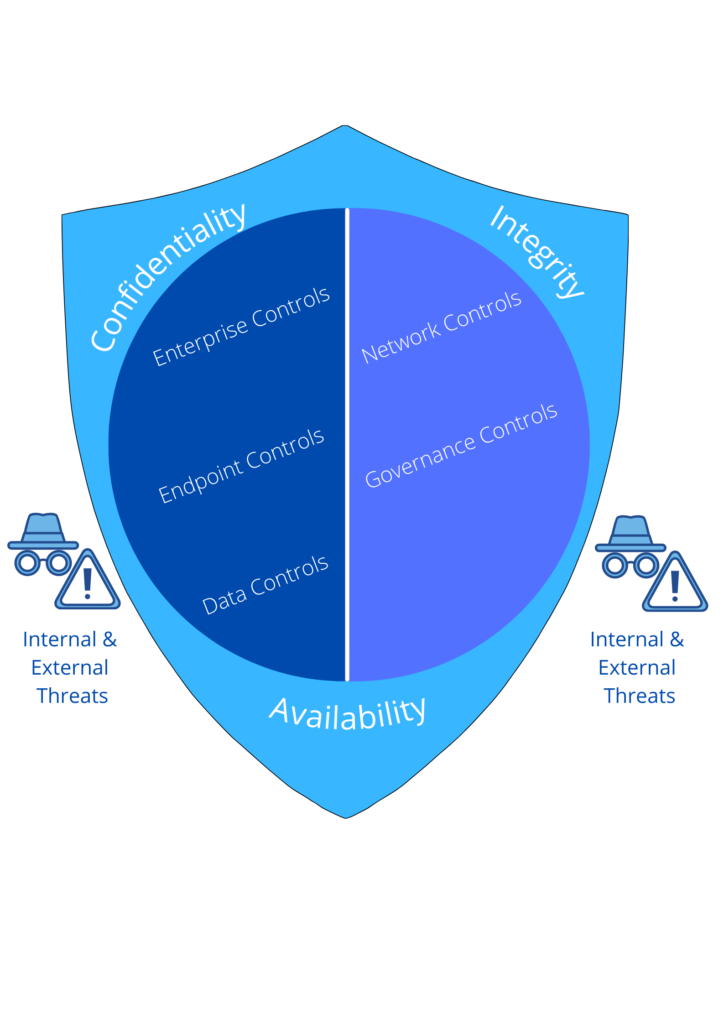
- Data Loss Prevention (DLP) and User Entity Behaviours Analytics (UEBA)
- Intrusion Detection and Prevention Systems (IDPS)/Deception
- Firewall Platform
- Network Control
- Unified Threat Management
- Web Application Firewall
- Web Fraud Prevention
- Web Security Gateway
- Managed Security Services
- Vulnerability Scans
- Certificate Authority (CA)/ Public Key Infrastructure (PKI) Solutions
- Cloud Security/ Cloud Access Service Broker (CASB)
- Distributed Denial of Service (DDOS) Security
- Email/ Domain-based Message Authentication, Reporting, and Conformance (DMARC) Security
- Border Gateway Protocol (BGP)/Domain Name Service (DNS)/Software Define Network (SDN) Security
- Network Monitoring
- Virtual Private Network (VPN)/Secure Access
- Anti-Malware Tools
- Endpoint Security
- Internet of Things (IoT) Security
- Mobile Security
- Password/Privilege Access Management
- Multi-Factor Authentication
- Voice Security
- Digital Risk Management
- Security Assessment
- Bug Bounty Support
- Cyber Insurance
- Governance Risk & Compliance (GRC) and Risk Management
- Incident Readiness and Incident Response
- Penetration Test/Simulation
- Security Information and Event Management (SIEM) Platform
- Threat Intelligence
- Security Training, Cyber Hygiene and Awareness
- Application Security
- Content Protection
- Data Destruction
- Data Encryption
- Digital Forensics
- Identity & Access Management (IAM) and Identity Platforms
- Compliance Support
- Vulnerability Management
- Security Consulting
